Critical Systems Protection
Anytime, Anywhere, with Any Device
Seamless access control and intuitive transactional verification …
Seamless Integrity
iCrypto is an E2E Trusted Digital Identity, Credentials and Access Management Platform, securing Essential Systems and Critical Infrastructure, that enables:
- Increased Security & Regulatory Compliance.
- Secures IoT transactions between People and Things.
- Minimal friction and increased Transaction Volume & Profitability.
- Increased Accountability & Operational Compliance.
Our Products
Just In Time Biometric Access Anytime, Anywhere with Any Device
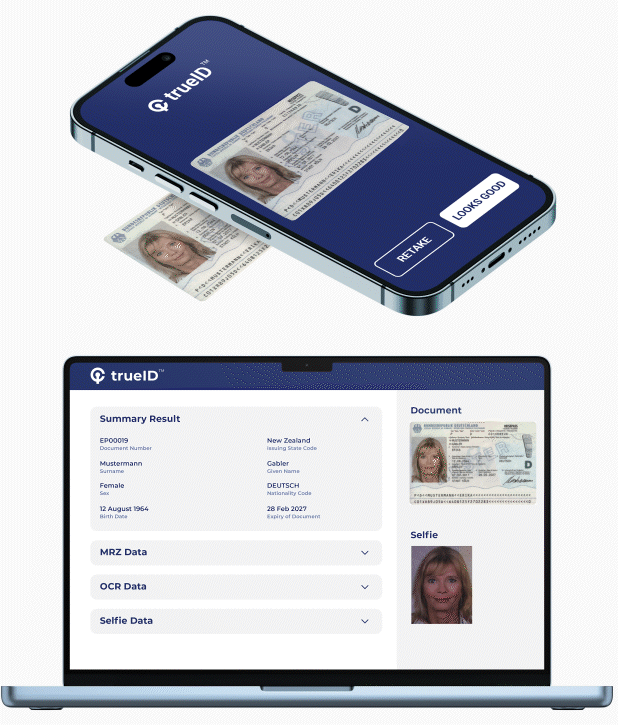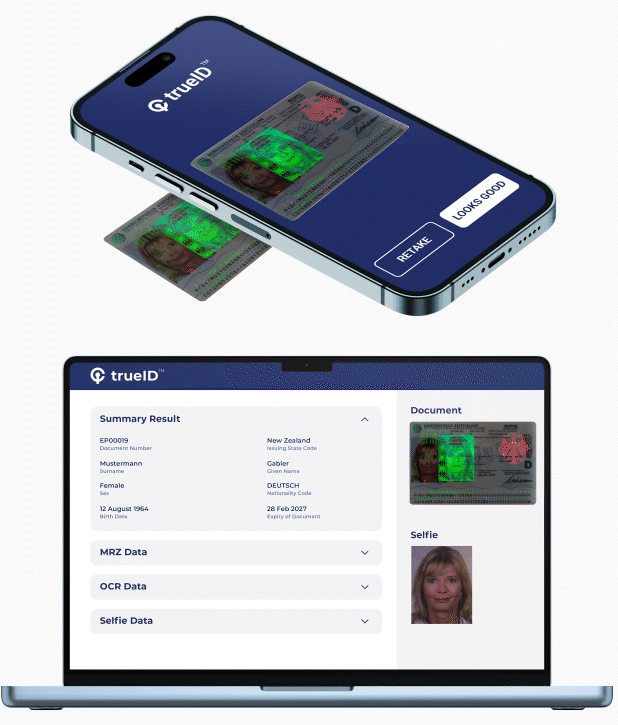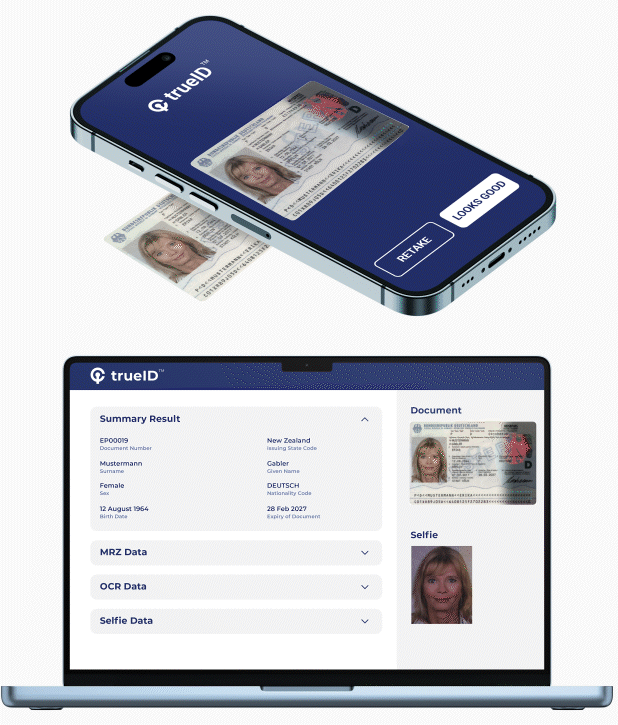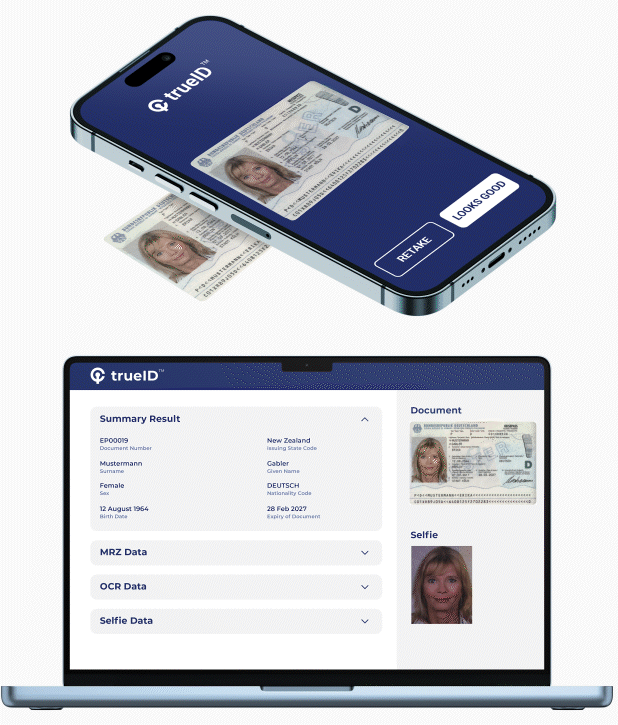
Provides vetting of users by using their mobile phone to capture face, scan Government ID, physical address, and / or accreditation. User identity is verified via Government Databases, Credit Bureau, and Public / Private Data Services. iCrypto automates this process into a digital workflow thereby allowing it to be inserted into user on-boarding, provisioning and other workflows. Some of its benefits include:
- Rapid onboarding of customers with frictionless, accurate and automated e-KYC verification.
- Protecting users from identity fraud, impersonation and cloning using next-generation AI-biometric verification.
- Increasing assurance and decreasing risk with AI document verification of 12,000 documents from 192 countries.
- Ensuring compliance to the most rigorous PII standards for processing and storage of confidential data.
iCrypto trueIDTM uses AI / ML Face Recognition, FIDO2 / WebAuthN, Multi-party Cryptography, Verifiable Credentials, and Distributed Identity secured by Blockchain to ensure the person behind a transaction is present and verified while protecting its privacy.
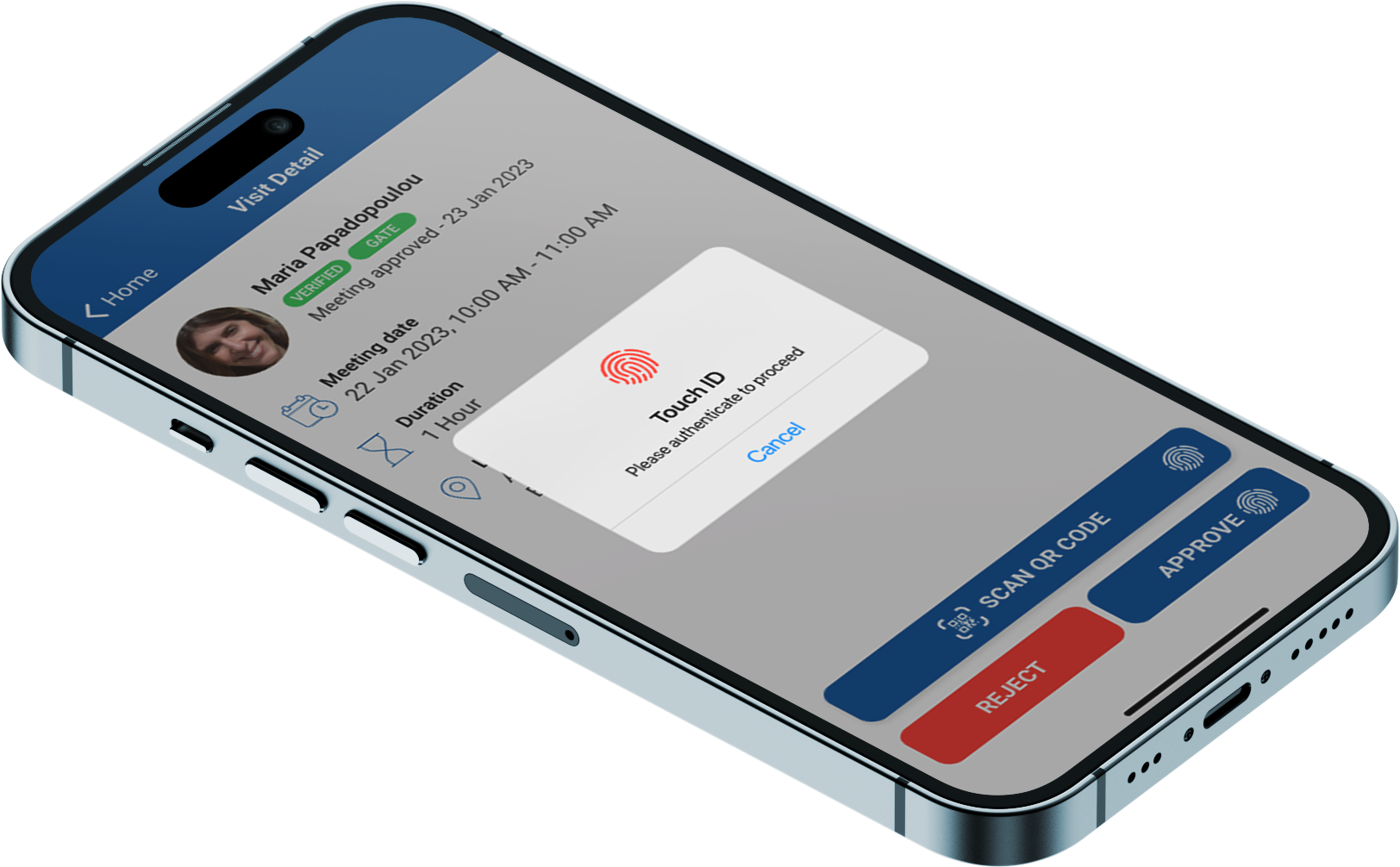
Secures access to physical sites, facilities, and installations by controlling that the right person is accessing the right site during the allocated time period for a valid reason. It provides an overlay security to existing installations of critical infrastructure by controlling identity of service personnel, mapping trouble tickets, securing the workflow, and operating physical access of e-locks via a mobile app. Some of its benefits include:
- Securing cyber-physical workflows, equipment and access from a single intuitive mobile user interface.
- Monitoring control and enforcing your standard operating procedures and service level agreements with precision.
- Empowering service delivery teams with targeted, purpose-built tools and information in a unified user experience.
- Unleashing the power of AI and analytics with intelligent workflows, automation, and optimization built into an easy-to-use interface.


iCrypto trueSATM protects critical infrastructure by layering Secure Biometric Access, Identity Verification, Lock Aggregation, Service-Level Agreement monitoring, and Standard Operating Procedure compliance / enforcement for industries such as Telecom, Utilities, Finance, and others.
Provides Just-In-Time one-time Access Credentials to individual users, devices, and applications that are used for authentication, access control, and for providing confidentiality. truePAMTM provides Continuous Authorization of essential workflow transactions for an organization to protect its Critical Systems. It is a centralized gatekeeper of credentials, privileges, and policies to an organization’s critical resources. Some of its benefits include:
- Implementing true zero-trust security by adding to the legacy perimeter security the enforcement of continuous authentication, authorization, and encryption for all transactions.
- Preventing phishing and impersonation by eliminating static credentials and utilizing Just-In-Time and ephemeral certificates backed by biometrics and hardware identity.
- Lowering the operational overhead of managing access and enforcing policy by consolidating humans and IoT privileges.
iCrypto truePAMTM provides an identity-based proxy for securing SSH to UNIX systems, RDP for Microsoft Windows, Kubernetes, and database access. It provides session recording / replay, Secrets Engine, AI / ML anomaly detection and secrets management.
Delivers a smarter and more powerful way to manage facilities security by providing an integrated cyber and physical state of the art access control based on identity awareness. It easily integrates with existing Physical Access Control Systems, enables contextual policy-based operation of door controllers and biometric Just-In-Time Access. Some of its benefits include:
- Modernizing your legacy PACS to automate physical access management and compliance.
- Mitigating external and insider threats by inserting identity at the core of your physical access management strategy.
- Reducing risk with self-service check-in, mobile credentialing, digital authentication, and geolocation tracking.
- Providing insight into physical space usage by using data.


iCrypto truePACSTM provides robust data analytics, streamlined workflows, identity management integrations, intelligent door control, AI / ML anomaly sensing, alerts and alarms, and powerful security features, so that you can protect people, property, and reputation.


Provides the full range of activities related to the creation of digital identities and maintenance of associated attributes, credential issuance for person or non-person entities, authentication, making access and authorization decisions based on authenticated trusted identities and associated attributes. It is a comprehensive solution to manage and govern identities of enterprise customers and workforce with consistent policies. It has phishing-resistant transaction level multifactor verification and password-less authentication with biometric verification using FIDO2 / WebAuthN devices.
iCrypto trueICAMTM is based on National Cyber Security Strategy (US-NCSS-2018) and is compliant to DoD ICAM Reference Architecture. It deploys the latest industry open standards such as OIDC, FIDO2, SAML, UMA, and SCIM.
- A seamless user experience with secure single sign-on, single logout and integrated credentials management
- Continuous fine-grained Just-In-Time authorization tailored to your users and their access context.
- Frictionless strong authentication to continuously and securely verify user in a zero-trust deployment.
iCrypto trueICAMTM is based on National Cyber Security Strategy (US-NCSS-2018) and is compliant to DoD ICAM Reference Architecture. It deploys the latest industry open standards such as OIDC, FIDO2, SAML, UMA, and SCIM.
Provides a distributed identity management framework that uses orchestration to manage multiple identity domains on multiple clouds within multiple silos. It provides organizations the ability to give the right people the right level of access to the right resources in the right context and then continuously monitor their audit trails using real-time forensics. Identity provisioning, synchronization, RBAC / ABAC / PBAC controls, organization and role management, data aggregation, approval processes, and auditing provide an organization E2E identity control and orchastration. Some of its benefits include:
- A complete solution to managing and govern identities of enterprise customers and workforce with consistent policies.
- Comprehensive lifecycle governance for all your identities – people, places and things – integrating into a single overlay solution.
- A configurable central admin console to manage all users, roles, entitlements and policies.

iCrypto trueIdMTM provides businesses with the tools to govern and automate critical identity processes, ensuring compliance, reducing risk, and enhancing operational efficiency. By centralizing and streamlining identity orchestration and management, trueIdM enables organizations to confidently navigate the complexities of today’s dynamic and interconnected IT environments, safeguarding sensitive data and ensuring that access controls align with business objectives.
Centralizes all enterprise policies for application and infrastructure into a scalable, distributed framework allowing complex real-world decision making. It decouples distributed enforcement from decision making and decouples policy from application code. truePolicy also provides a code-as-policy framework and allows authoring and testing before deployment. Some of its benefits include:
- Automating data governance, protecting corporate assets, preventing misuse of APIs.
- Implementing fine-grained real-time dynamic control over API access from applications and users.
- Centrally configuring your dynamic policies and allowing administration by business users in a low code environment.
- Map dynamic attribute-based policies to provide definitive evidence for compliance reports & regulations.
iCrypto truePolicyTMclearly provides an open and pluggable interface for policies, resource connectors, workflows and data schema. It supports the latest standards such as OIDC, SCIM, FIDO2 and LDAP to provide a system scalable to over 1 billion identities.
Provides credentials Proof using distributed cryptography and Decentralized Identity standards. The solution biometrically identifies the person and maps their identity attributes to a mobile credential. The person then has digital, portable, immutable, non-refutable cryptographic proof of their identity and associated credentials that allows to participate in any workflow that requires proof of identity and / or credentials. Some of its benefits include:
- Creating global applications that are future-proof with mobile biometric and Open Source standards.
- Developing user-centric solutions with wide-spread adoption by mapping physical user to mobile digital Identity secured by blockchain.
- Enabling frictionless access to a new generation of secure and trusted eServices by leveraging distributed identity and trusted credentials.
- Providing non-repudiation for high security applications via usage of biometrics and blockchain signatures for any identity data access.
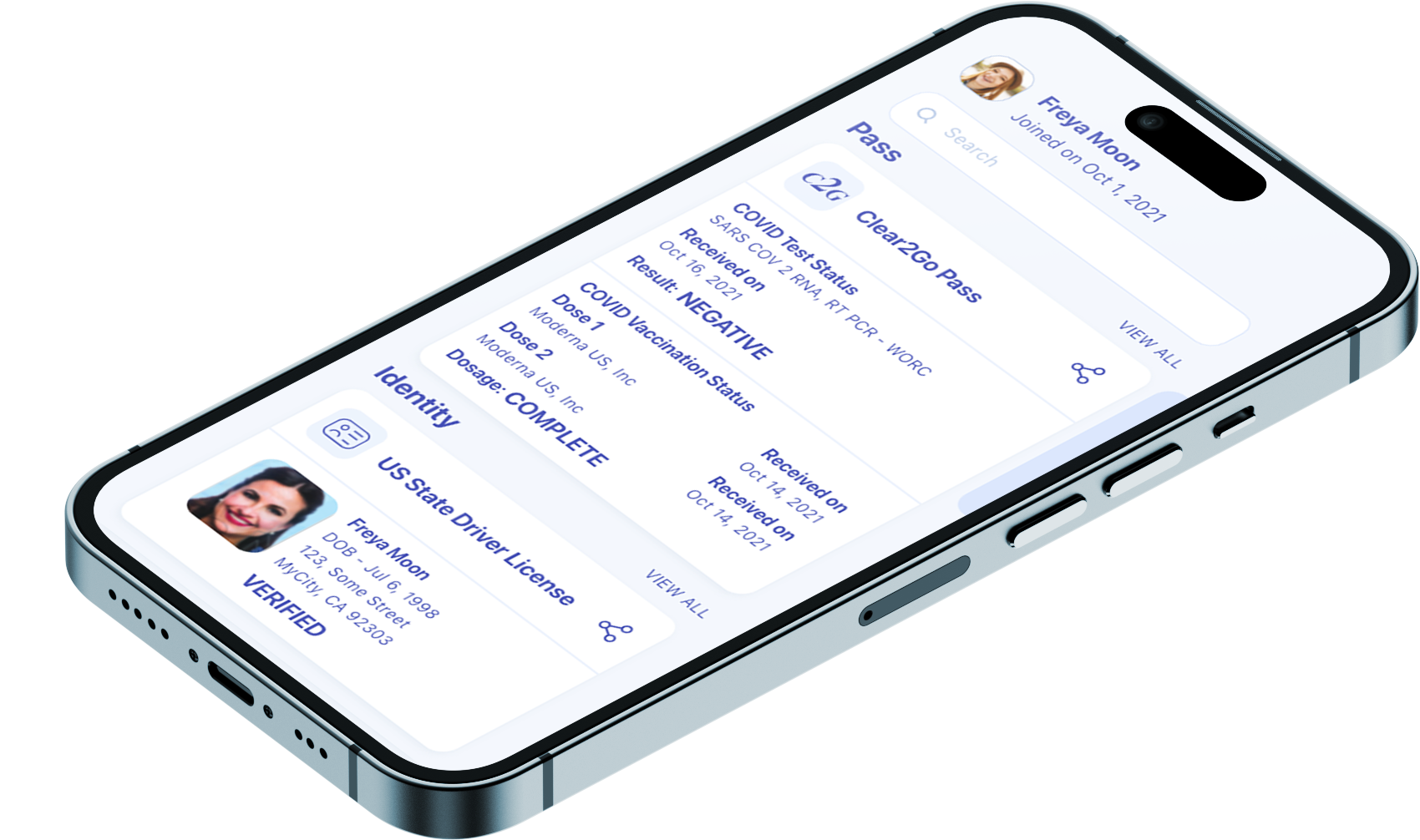
iCrypto Clear2GoTM provides Proof of Possession, allows users to prove elements of their identity – age, medical stats, education, accreditation, financial – with assurance that the data is irrefutable, non-repudiated, immutable, and tamper-evident. It enables one-click frictionless access to a new generation of eServices, exceeding compliance directives (GDPR, CCPA) for privacy, consent, and security.

















